What is a Bypass TAP?
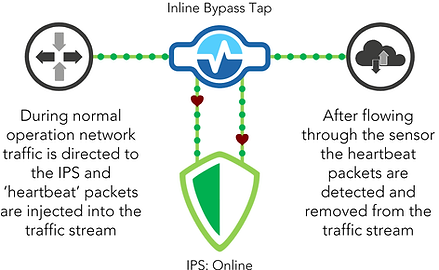
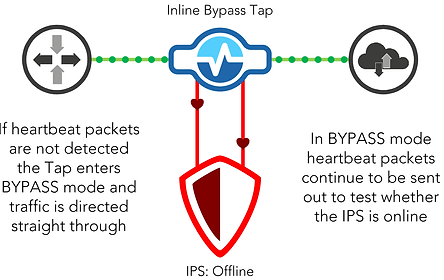
A bypass TAP, sometimes referred to as a Bypass Switch, has consistent heartbeats that are sent to an inline security appliance. These heartbeats indicate the functionality of the security appliance: regular beats mean the bypass TAP is functioning well. If the beats are not returned to the bypass TAP (see below) the TAP automatically bypasses the appliance to allow the packets to be sent through, no matter how high the traffic is. It is also able to detect the status of the appliance, so when it comes back online, this is detected by the TAP and traffic is once again directed through the appliance.
When an IPS or other Inline Appliance is installed behind a V-Line™ TAP, the TAP continually checks the status of the appliance and if it is online, will direct traffic through it. If the appliance goes for maintenance or update, or for any such reason, the TAP will automatically bypass the appliance and direct traffic straight through to the network.